Role-Based Access in CRM: Least Privilege by Design is a critical framework for safeguarding sensitive customer relationship management (CRM) data. This approach focuses on controlling user access based on their defined roles within an organization, significantly enhancing data security and compliance. The implementation of ‘least privilege’ ensures users only have the necessary access rights to perform their job functions, minimizing the potential attack surface and reducing the risk of data breaches or unauthorized modifications.
This methodology contrasts with less secure models where users might have excessive permissions, leading to potential data exposure. This exploration will delve into the core principles of Role-Based Access Control (RBAC), the ‘least privilege’ principle, and their practical application within a CRM environment. We will examine the design of roles and permissions, best practices for implementation, common challenges, and how RBAC supports compliance with regulations like GDPR and CCPA.
Furthermore, we will discuss auditing, monitoring, CRM system selection, advanced techniques like dynamic role assignment, and the impact of RBAC on CRM integrations.
Introduction to Role-Based Access Control (RBAC) in CRM
Role-Based Access Control (RBAC) is a security model that regulates user access to system resources based on their assigned roles within an organization. This approach simplifies access management, enhances security, and improves compliance by aligning user permissions with their job responsibilities. In the context of a Customer Relationship Management (CRM) system, RBAC ensures that users only have access to the data and functionalities necessary for their roles, mitigating the risk of unauthorized data access or modification.
Fundamental Concept of RBAC in CRM
RBAC in CRM centers around the principle of assigning permissions to roles, rather than to individual users. These roles are then assigned to users based on their job functions. This allows for efficient management of user access and simplifies the process of granting or revoking permissions.The core components of RBAC in a CRM system include:
- Users: Individuals who interact with the CRM system.
- Roles: Collections of permissions that define what actions a user can perform and what data they can access. Examples include “Sales Representative,” “Marketing Manager,” or “Customer Service Agent.”
- Permissions: Specific actions or data access rights within the CRM. Examples include “View Contacts,” “Edit Opportunities,” “Create Cases,” or “Export Reports.”
- Role Assignment: The process of assigning users to roles.
This model provides a structured approach to access control. For instance, a Sales Representative role might have permissions to view, create, and edit contact and opportunity records, but not access financial data or delete customer records. In contrast, a Marketing Manager role might have permissions to view, analyze, and export customer data for marketing campaigns, but not modify sales opportunities.
Enhancing Data Security and Compliance with RBAC
RBAC significantly enhances data security and facilitates compliance with regulatory requirements within a CRM environment. By limiting access to only the necessary information, RBAC reduces the risk of data breaches, accidental data modification, and unauthorized data access.Here are some examples:
- Data Breach Prevention: If a Sales Representative’s account is compromised, the attacker would only have access to the data and functionalities associated with that role. They wouldn’t be able to access sensitive financial data or other confidential information that a higher-level role might have access to.
- Compliance with Data Privacy Regulations: RBAC supports compliance with regulations such as GDPR and CCPA by allowing organizations to control access to personally identifiable information (PII). For example, only authorized personnel in the Customer Service or Data Protection Officer role can access and manage PII data.
- Reduced Insider Threats: RBAC minimizes the potential damage from insider threats by restricting access to sensitive data based on the principle of least privilege. A disgruntled employee would have limited access to sensitive information, reducing the risk of data theft or sabotage.
- Auditability: RBAC facilitates audit trails, making it easier to track user activities and identify potential security breaches or policy violations. Auditing capabilities can be integrated to log who accessed what data and when.
Benefits of RBAC over Other Access Control Models in CRM
Compared to other access control models, such as Discretionary Access Control (DAC) or Mandatory Access Control (MAC), RBAC offers several advantages in the context of a CRM system. DAC relies on the data owner to set access permissions, which can be cumbersome and error-prone. MAC, while more secure, is complex to implement and manage.Here’s a comparison:
- Simplified Access Management: RBAC simplifies access management by assigning permissions to roles, rather than individual users. This makes it easier to manage user access, especially in large organizations with frequent employee turnover.
- Improved Efficiency: RBAC streamlines the process of granting or revoking permissions. When a user’s role changes, the administrator only needs to change the role assignment, rather than modifying individual permissions.
- Enhanced Security: By adhering to the principle of least privilege, RBAC minimizes the attack surface and reduces the risk of unauthorized access to sensitive data.
- Scalability: RBAC is highly scalable and can easily accommodate changes in organizational structure or business processes.
- Cost-Effectiveness: RBAC reduces the administrative overhead associated with access management, leading to cost savings.
RBAC also supports the concept of separation of duties, ensuring that no single user has complete control over critical processes. For example, a Sales Representative may be able to create an opportunity but not approve a discount. This separation of duties reduces the risk of fraud and error.
Understanding the ‘Least Privilege’ Principle
The ‘least privilege’ principle is a cornerstone of secure system design, especially critical in Customer Relationship Management (CRM) systems where sensitive customer data resides. This principle dictates that users, processes, and systems should only be granted the minimum level of access necessary to perform their intended functions. This minimizes the potential damage from security breaches, both intentional and accidental.
Defining the ‘Least Privilege’ Principle and Its Significance
The ‘least privilege’ principle, at its core, limits user access rights to the bare minimum required for their job duties. It is not simply about restricting access; it is a proactive approach to security, aiming to reduce the attack surface.This principle is significant because:
- It reduces the impact of a security breach: If a user’s account is compromised, the attacker’s capabilities are limited to the permissions granted to that specific user. This confines the scope of the breach.
- It minimizes insider threats: By limiting what employees can access, the risk of malicious or accidental data exposure is decreased. A disgruntled employee, for example, would be unable to access sensitive information outside their defined role.
- It improves compliance with regulations: Many data privacy regulations, such as GDPR and HIPAA, mandate access controls that align with the ‘least privilege’ principle.
- It simplifies auditing: Tracking and auditing access becomes easier when permissions are tightly controlled and clearly defined.
Minimizing the Attack Surface in a CRM
Implementing ‘least privilege’ directly shrinks the attack surface within a CRM. The attack surface is the total number of vulnerabilities and potential entry points an attacker could exploit.The principle minimizes the attack surface in the following ways:
- Reduced Scope of Compromise: When a user account is breached, the attacker only gains access to the resources the user is authorized to use. This prevents them from accessing the entire CRM database, protecting sensitive information.
- Restricted Data Exposure: Limiting data access to only what is necessary prevents unauthorized viewing, modification, or deletion of critical customer information. This is especially important for financial data, personal details, and confidential communications.
- Lowered Risk of Lateral Movement: If an attacker gains access to a system, they often try to move laterally to other systems within the network. ‘Least privilege’ makes this more difficult because the compromised account lacks the permissions needed to access other systems.
- Simplified Vulnerability Management: With fewer privileges granted, the impact of a vulnerability is lessened. For instance, if a vulnerability exists in a CRM module that only certain users can access, the damage is contained.
Consequences of Not Adhering to the ‘Least Privilege’ Principle in a CRM
Failing to implement ‘least privilege’ in a CRM can lead to significant security and operational risks. The consequences can range from minor data leaks to catastrophic breaches.Consider these scenarios:
- Data Breaches and Regulatory Fines: A CRM administrator with excessive privileges could be targeted by attackers. If the administrator’s account is compromised, the attacker could potentially access all customer data, leading to a major data breach. The organization would face significant fines and reputational damage, potentially impacting its future operations.
- Insider Threats and Data Leakage: An employee with overly broad access could accidentally or maliciously expose sensitive customer information. For example, a sales representative with administrator privileges could inadvertently download a customer list containing personally identifiable information (PII) and share it externally. This would violate privacy regulations.
- Unauthorized Data Modification: Employees with excessive permissions could alter customer data, potentially impacting marketing campaigns or causing financial losses. A marketing manager with edit access to the billing information might accidentally modify payment details, resulting in lost revenue and customer dissatisfaction.
- System Downtime and Service Disruption: A compromised account with extensive permissions could lead to system instability or even complete shutdown. An attacker could delete critical data or disable core CRM functions, disrupting business operations.
- Reputational Damage and Loss of Customer Trust: Any data breach or security incident can erode customer trust. If a CRM is compromised, customers may lose confidence in the organization’s ability to protect their data, leading to customer churn and decreased revenue.
Implementing RBAC in a CRM

Source: pikist.com
Implementing Role-Based Access Control (RBAC) in a Customer Relationship Management (CRM) system is a critical step in securing sensitive data and ensuring operational efficiency. This involves a systematic approach that considers user roles, permissions, and ongoing maintenance. Successfully integrating RBAC requires careful planning and consistent execution to provide optimal data security and user experience.
Essential Steps for RBAC Implementation
Implementing RBAC in a CRM involves a structured process. This process ensures that access controls are effectively applied and aligned with the organization’s security policies and operational requirements.
- Role Definition: The initial step involves identifying and defining the various roles within the CRM system. This should be based on job functions, responsibilities, and data access needs. For instance, roles might include Sales Representatives, Marketing Managers, Customer Service Agents, and System Administrators. Each role should be clearly documented with its associated responsibilities.
- Permission Mapping: Once roles are defined, the next step is to map specific permissions to each role. This involves determining which data elements each role needs to access, modify, or delete. This includes specifying access to CRM objects (e.g., accounts, contacts, opportunities), fields, and functionalities (e.g., reporting, data import).
- User Assignment: Users are then assigned to the appropriate roles based on their job functions. This is where the “least privilege” principle is applied. Users should only be granted the minimum level of access necessary to perform their duties.
- Implementation and Testing: The RBAC model is implemented within the CRM system. Thorough testing is crucial to ensure that the access controls function as intended. This testing should include various scenarios to verify that users can access the data and functionalities they need and that they are prevented from accessing data they should not have.
- Training and Documentation: Proper training for users and administrators is essential. Users need to understand their roles and the limitations of their access. Administrators need to know how to manage roles, permissions, and user assignments. Comprehensive documentation should be created and maintained to guide the implementation and ongoing management of RBAC.
Importance of Regular Audits and Reviews
Regular audits and reviews of role assignments and permissions are essential for maintaining the effectiveness of RBAC. These practices help to identify and address potential security vulnerabilities, ensure compliance with regulations, and adapt to changing business needs.
Audits and reviews should be performed periodically. The frequency can vary depending on the sensitivity of the data and the organization’s risk profile. For example, organizations dealing with highly sensitive customer data might conduct audits quarterly, while others may perform them annually. These reviews should include a thorough examination of:
- Role Assignments: Verify that users are still assigned to the appropriate roles and that their roles align with their current job responsibilities. Changes in job duties should trigger a review of role assignments.
- Permissions: Review the permissions associated with each role to ensure they are still appropriate. Over time, permissions can become overly permissive or insufficient.
- Access Logs: Analyze access logs to identify any unusual or suspicious activity. This can help detect potential security breaches or unauthorized access attempts.
- Compliance: Ensure that the RBAC implementation complies with relevant regulations and industry standards, such as GDPR, HIPAA, or PCI DSS, depending on the industry and the type of data managed by the CRM.
Procedure for Managing User Access Requests and Role Modifications
A well-defined procedure for managing user access requests and role modifications is crucial for maintaining a secure and efficient RBAC implementation. This procedure should ensure that all changes are authorized, tracked, and implemented in a consistent manner.
The procedure should include the following steps:
- Request Submission: All access requests and role modification requests should be submitted through a formal process. This typically involves a request form that includes the user’s name, the requested access or modification, the justification for the request, and the approval of the user’s manager.
- Approval Workflow: Requests should follow a defined approval workflow. The workflow should include the appropriate levels of authorization, such as the user’s manager and the system administrator. The workflow should also include a mechanism for documenting the approval process.
- Implementation: Once approved, the requested changes should be implemented within the CRM system. This should be done by authorized personnel, such as the system administrator. The implementation process should be documented to provide an audit trail.
- Verification: After the changes are implemented, the system administrator or a designated reviewer should verify that the changes were made correctly and that the user has the appropriate access.
- Documentation and Archiving: All requests, approvals, and implementation details should be documented and archived. This documentation provides an audit trail and can be used for future reference. The documentation should include the date of the request, the user’s name, the type of access requested, the justification, the approval process, and the implementation details.
Common Challenges and Solutions in RBAC Implementation
Implementing Role-Based Access Control (RBAC) in a Customer Relationship Management (CRM) system, while offering significant security and operational benefits, presents several challenges. Overcoming these obstacles is crucial for realizing the full potential of RBAC and ensuring the CRM environment remains secure, efficient, and compliant with relevant regulations. The following sections will detail common challenges and explore effective solutions.
User Onboarding and Training
User onboarding, the process of integrating new users into the CRM system, and subsequent training, are significant hurdles in RBAC implementation. A poorly executed onboarding process can lead to incorrect role assignments, creating security vulnerabilities or hindering user productivity. Effective training is vital for users to understand their roles, permissions, and responsibilities within the system.To mitigate these challenges, consider the following:
- Automated Role Assignment: Implement automated role assignment based on predefined criteria, such as department, job title, or team. This reduces the risk of human error and speeds up the onboarding process. For example, when a new sales representative is added to the CRM, the system automatically assigns the “Sales Representative” role, granting them access to relevant sales data and tools.
- Role-Specific Training: Develop role-specific training modules that clearly Artikel the permissions, responsibilities, and system functionalities relevant to each role. This ensures users understand how to effectively utilize the CRM while adhering to security protocols. For instance, a training module for the “Marketing Manager” role should cover campaign management, data analysis, and reporting functionalities, as these are the tasks primarily performed by individuals in this role.
- Regular Audits and Reviews: Conduct regular audits of user roles and permissions to identify and rectify any discrepancies or inappropriate access. This helps maintain the integrity of the RBAC system over time. The audits should involve a review of user activity logs, role assignments, and the effectiveness of training programs.
- User-Friendly Interface: Ensure the CRM system has a user-friendly interface, making it easy for users to navigate and understand their assigned roles and permissions. This reduces the likelihood of users accidentally accessing or modifying data they are not authorized to.
Role Creep
Role creep, the gradual expansion of user permissions over time, is a common problem. It occurs when users accumulate more permissions than they need, potentially leading to security breaches and data exposure. This can happen through frequent ad-hoc requests for additional access, or through poorly designed role definitions that grant excessive privileges from the outset.Addressing role creep requires a proactive approach:
- Regular Permission Reviews: Implement a schedule for periodic reviews of user permissions. This involves examining the permissions assigned to each role and assessing whether they are still necessary and appropriate. The frequency of these reviews should be determined based on the sensitivity of the data and the criticality of the CRM system.
- Principle of Least Privilege Enforcement: Strictly adhere to the principle of least privilege, granting users only the minimum necessary permissions to perform their job functions. This limits the potential damage if a user account is compromised.
- Role Definition Refinement: Continuously refine role definitions based on user needs and evolving business requirements. This involves regularly updating roles to ensure they accurately reflect the tasks and responsibilities of each user.
- Automated Permission Management: Use automation tools to manage permissions and detect potential role creep. These tools can identify users with excessive permissions and alert administrators to take corrective action.
Permission Conflicts
Permission conflicts arise when different roles have conflicting permissions, leading to unexpected behavior or security vulnerabilities. This can happen when roles are poorly designed or when permissions are not carefully managed. For example, one role might grant access to modify customer data, while another role might restrict access to the same data.Resolving permission conflicts requires careful planning and management:
- Thorough Role Design: Before implementing RBAC, meticulously design roles and their associated permissions. This includes identifying the specific tasks each role will perform and the data they will need to access.
- Permission Matrix: Create a permission matrix that maps roles to permissions, making it easy to visualize and manage potential conflicts. This matrix should clearly show which roles have access to which data and functionalities.
- Testing and Validation: Rigorously test the RBAC implementation to identify and resolve any permission conflicts before deploying the system to production. This involves simulating various user scenarios and verifying that the system behaves as expected.
- Regular Monitoring and Adjustment: Continuously monitor user activity and permission assignments to detect and resolve any emerging permission conflicts. This involves regularly reviewing user access logs and making adjustments to role definitions as needed.
Complexity in Permission Structures
Managing complex permission structures in a CRM can be challenging, especially in large organizations with diverse user roles and data requirements. As the number of roles and permissions increases, it becomes more difficult to maintain and troubleshoot the RBAC system.Several approaches can be used to manage complex permission structures:
- Hierarchical Role Structures: Organize roles into a hierarchy, with broader roles at the top and more specific roles at the bottom. This simplifies permission management by allowing permissions to be inherited from parent roles. For instance, a “Sales Manager” role could inherit permissions from a “Sales Representative” role, plus additional permissions specific to management tasks.
- Role Mining: Analyze user activity and identify common patterns of access to define new roles or refine existing ones. Role mining can help identify hidden or underutilized roles, which can improve security and operational efficiency.
- Attribute-Based Access Control (ABAC): Consider implementing ABAC in conjunction with RBAC for more granular control over permissions. ABAC uses attributes of users, resources, and the environment to make access control decisions, allowing for more complex and flexible permission policies. For example, access to a customer record could be granted based on the user’s department, the customer’s location, and the time of day.
- Centralized Permission Management Tools: Utilize specialized tools for managing permissions, which can simplify the process of defining, assigning, and auditing roles. These tools often provide features such as role modeling, permission mapping, and access request workflows.
RBAC and Data Compliance
Source: technofaq.org
Role-Based Access Control (RBAC) is a critical component in ensuring compliance with data privacy regulations. By controlling access to sensitive data within a CRM system, RBAC helps organizations meet the requirements of regulations like the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA). Effective RBAC implementation is not just a technical requirement; it’s a strategic necessity for building trust with customers and avoiding significant legal penalties.
RBAC Support for Data Privacy Regulations
RBAC inherently supports compliance with data privacy regulations by limiting data access to only those users who need it to perform their jobs. This “least privilege” approach minimizes the risk of unauthorized access, data breaches, and misuse of personal data. This aligns directly with the core principles of GDPR and CCPA, which emphasize data minimization, purpose limitation, and security.
Configuring RBAC for Compliance in a CRM
Configuring RBAC to meet specific compliance requirements involves several key steps. The process begins with a thorough understanding of the relevant regulations and the organization’s data processing activities. This understanding informs the creation of roles, the assignment of permissions, and the ongoing monitoring of access controls.Here’s a breakdown of how to configure RBAC for GDPR and CCPA compliance:
- Data Mapping and Classification: Identify and classify all personal data stored within the CRM. This includes determining the sensitivity level of each data element (e.g., contact information, financial details, health records). Data mapping helps understand where the data resides and how it is used.
- Role Definition: Define roles based on job functions and data access needs. For example, a “Sales Representative” role might have access to contact information and sales history, while a “Marketing Analyst” role might have access to aggregated customer data for campaign analysis but not individual contact details.
- Permission Assignment: Grant permissions to each role based on the principle of least privilege. This means users should only have access to the data and functionalities necessary for their specific tasks. For instance, a sales representative might be granted “read” and “write” access to customer contact information but not “delete” access.
- Audit Trails and Logging: Implement robust audit trails to track user access and data modifications. This allows for monitoring and detection of unauthorized access or data breaches. The CRM should log all user actions, including data access, modification, and deletion, along with timestamps and user identities.
- Data Subject Rights Management: Configure RBAC to support data subject rights, such as the right to access, rectify, and erase personal data. Roles should be designed to allow authorized users to fulfill these requests efficiently. For example, a “Data Protection Officer” role might be granted specific permissions to manage data subject requests within the CRM.
- Regular Review and Updates: Regularly review and update roles and permissions to reflect changes in job responsibilities, data processing activities, and regulatory requirements. This includes conducting periodic access reviews to ensure that users still have the appropriate level of access.
Key Compliance Considerations for RBAC Design in CRM
When designing and implementing RBAC in a CRM system, several key compliance considerations must be addressed. These considerations are essential for ensuring that the system meets the requirements of data privacy regulations and protects sensitive customer data.Here’s a bullet point list:
- Data Minimization: Ensure that roles and permissions are designed to provide users with access only to the data necessary for their job functions. This minimizes the risk of unnecessary data collection and storage.
- Purpose Limitation: Align data access with the specific purposes for which the data is collected and processed. Access should be restricted to users involved in those specific purposes.
- Data Security: Implement robust security measures, including encryption, access controls, and regular security audits, to protect data from unauthorized access, disclosure, or loss.
- Data Subject Rights: Design RBAC to support data subject rights, such as the right to access, rectify, erase, and restrict processing of personal data.
- Transparency and Accountability: Maintain clear documentation of roles, permissions, and data access controls. Implement processes for monitoring and auditing data access to ensure accountability.
- Training and Awareness: Provide regular training to users on data privacy regulations, RBAC policies, and their responsibilities for protecting customer data.
- Vendor Management: When using third-party CRM systems or services, ensure that vendors have adequate security measures and data privacy practices in place. Review vendor contracts to ensure compliance with data privacy regulations.
- Regular Audits and Reviews: Conduct regular audits of RBAC implementation to identify and address any vulnerabilities or compliance gaps. Review roles, permissions, and access controls regularly to ensure they remain appropriate.
Auditing and Monitoring RBAC in CRM
Effective auditing and monitoring are crucial for maintaining the security and integrity of a CRM system that employs Role-Based Access Control (RBAC). They provide visibility into user activities, permission changes, and potential security threats, allowing organizations to proactively identify and mitigate risks. A robust auditing and monitoring strategy ensures compliance with regulatory requirements and supports continuous improvement of the security posture.
Methods for Auditing User Access and Permission Changes
Auditing user access and permission changes involves tracking all modifications related to user roles and their associated privileges. This allows administrators to understand who has access to what data and when those permissions were granted or altered.
- Activity Logging: Implementing comprehensive activity logging is fundamental. This involves recording every user action within the CRM, including logins, data modifications, record views, and permission changes. The logs should include timestamps, user identities, the specific actions performed, and the data affected.
- Role and Permission Change Tracking: Every modification to roles, permissions, and access levels must be meticulously tracked. This includes recording the user who made the change, the date and time of the change, the previous and new values of the permission or role, and a description of the change.
- Access Request and Approval Auditing: When access requests require approval, the auditing process should encompass the entire workflow, from the initial request to the final approval or denial. This should include the requestor, the approver, the date and time of the request, the justification for the access, and the final decision.
- Regular Review and Analysis: Auditing is not a one-time activity; it’s an ongoing process. Regular review and analysis of audit logs are essential to identify anomalies, potential security breaches, and areas for improvement in the RBAC implementation. This includes looking for unusual access patterns, unauthorized permission changes, and failed login attempts.
Demonstration of Monitoring User Activity to Detect Potential Security Breaches
Monitoring user activity is critical for identifying and responding to potential security breaches. This involves analyzing user behavior patterns and comparing them against established baselines to detect suspicious activities.
- Anomaly Detection: Implement systems that detect unusual user behavior, such as accessing data outside of their assigned roles, accessing data at unusual times, or exceeding the frequency of data access. This requires establishing baseline user behavior and setting alerts for deviations.
- Login Monitoring: Monitor all login attempts, including successful and failed logins. Track the IP addresses, devices, and locations of logins. A sudden increase in failed login attempts from a specific IP address or location could indicate a brute-force attack.
- Data Access Monitoring: Track all data access events, including the type of access (view, edit, delete), the data accessed, and the user who accessed it. This helps identify unauthorized data access or data exfiltration attempts.
- Alerting and Notification: Configure alerts and notifications for suspicious activities, such as unauthorized access attempts, privilege escalations, or unusual data access patterns. Alerts should be sent to security personnel or system administrators for immediate investigation.
- Real-time Monitoring Dashboards: Utilize real-time monitoring dashboards that provide a consolidated view of user activity, security events, and system performance. These dashboards should display key metrics, such as login attempts, data access events, and alert status.
Examples of Reports to Track RBAC Effectiveness
Generating reports is crucial for evaluating the effectiveness of the RBAC implementation and identifying areas for improvement. These reports provide valuable insights into user access patterns, permission changes, and potential security risks.
- User Access Review Report: This report lists all users and their assigned roles, along with a summary of their permissions. It should include information about the date of the last access and the types of data they can access. This report helps identify users with excessive or unnecessary permissions.
- Permission Change Audit Report: This report details all changes to user roles and permissions, including the user who made the change, the date and time of the change, the previous and new values of the permission or role, and a description of the change. This helps track permission modifications and identify unauthorized changes.
- Data Access Audit Report: This report tracks all data access events, including the user, the data accessed, the type of access (view, edit, delete), and the date and time of access. This report helps identify potential data breaches or unauthorized data access.
- Login Activity Report: This report summarizes login activity, including successful and failed login attempts, login locations, and login times. This helps identify potential security threats, such as brute-force attacks or unauthorized access attempts.
- Compliance Report: This report summarizes the organization’s compliance with relevant regulations, such as GDPR or HIPAA, based on the RBAC implementation and audit data. It should include information about user access, data access, and permission changes, and demonstrate adherence to regulatory requirements.
- Role-Based Access Control Effectiveness Report: This report assesses the overall effectiveness of the RBAC implementation. It may include metrics such as the number of users with excessive permissions, the frequency of permission changes, the number of security incidents, and the time to detect and respond to security incidents.
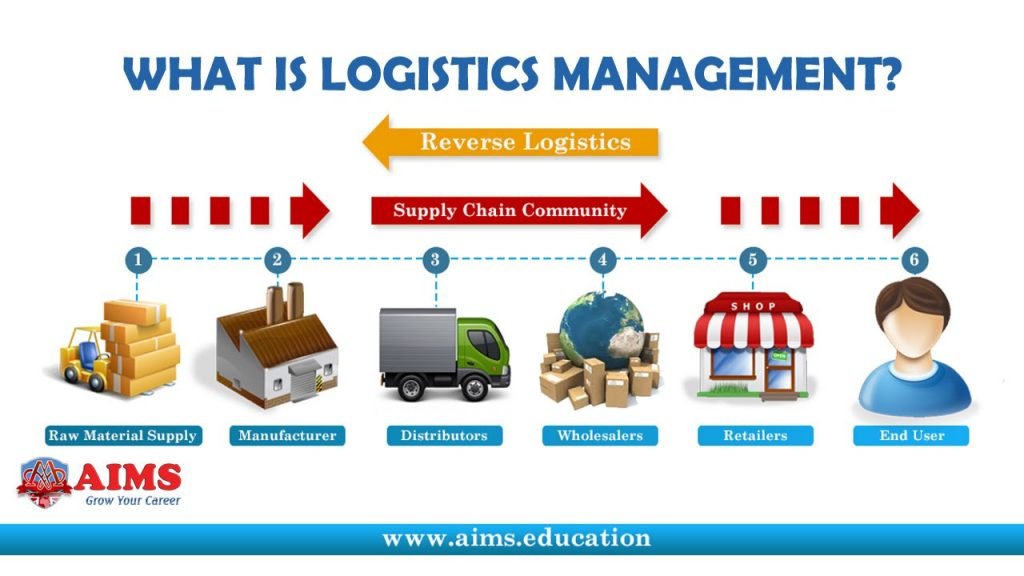
Role-Based Access Control and CRM System Selection: Role-Based Access In CRM: Least Privilege By Design
Selecting a Customer Relationship Management (CRM) system is a critical decision for any organization. The chosen system should not only meet current needs but also provide the flexibility and security required for future growth. A key consideration during this selection process is the CRM’s Role-Based Access Control (RBAC) capabilities. Effective RBAC ensures data security, compliance with regulations, and efficient user management.
Evaluating RBAC Capabilities During CRM System Selection
The evaluation of a CRM system’s RBAC features should be a systematic process. This process involves assessing the functionalities offered by different vendors to determine how well they align with an organization’s specific security and operational requirements. Thorough evaluation ensures that the selected CRM supports the necessary access controls to protect sensitive customer data and maintain data integrity.
- Role Definition and Customization: Assess the flexibility in defining roles.
- Granular Permissions: Examine the level of detail in permission settings.
- User Assignment and Management: Evaluate the ease of user assignment and management.
- Role Hierarchy: Determine the availability of role hierarchies.
- Auditing and Reporting: Investigate the auditing and reporting capabilities.
The CRM should allow administrators to create custom roles beyond predefined ones. The ability to tailor roles to specific job functions and responsibilities is essential. For example, a sales organization might need roles like “Sales Manager,” “Sales Representative,” and “Sales Support,” each with different levels of access to customer data, sales reports, and system settings. The system should also allow for modifications to these roles as business needs evolve.
The CRM should provide granular control over permissions. This includes the ability to define access rights at the field level, allowing administrators to restrict which users can view, edit, or delete specific data fields. For instance, sensitive information like Social Security numbers or financial details should be restricted to authorized personnel only. The system should support “read,” “write,” “create,” and “delete” permissions for each object and field.
The system should provide intuitive tools for assigning users to roles and managing user access. Features like bulk assignment, role inheritance (where permissions from a parent role are automatically inherited by child roles), and the ability to temporarily override permissions are beneficial. Efficient user management reduces administrative overhead and minimizes the risk of human error.
A role hierarchy allows for the creation of a tiered structure of roles, where higher-level roles inherit permissions from lower-level roles. This simplifies permission management and aligns with organizational structures. For example, a “Regional Sales Manager” role might inherit the permissions of a “Sales Manager” role, plus additional permissions related to managing regional sales data.
The CRM should provide comprehensive auditing and reporting features to track user activity and identify potential security breaches. This includes logging user logins, data access, and any changes made to records. Audit trails are crucial for compliance with regulations like GDPR and CCPA. The ability to generate reports on user activity and access patterns is also essential for monitoring and improving security.
Assessing the Robustness and Flexibility of CRM RBAC Features
The robustness and flexibility of a CRM’s RBAC features are crucial for long-term security and adaptability. A robust system is one that can withstand security threats and adapt to changing business requirements. Flexibility allows for easy modification and expansion of access controls.
- Scalability: Examine how the RBAC system handles increasing numbers of users and data.
- Customization Options: Assess the degree to which RBAC can be tailored to specific business processes.
- Integration Capabilities: Determine if the RBAC system integrates with other security systems.
- Security Features: Evaluate the built-in security features of the RBAC system.
As an organization grows, the number of users and the volume of data will increase. The RBAC system must scale effectively to handle this growth without compromising performance or security. This includes the ability to add new roles, assign users to roles, and manage permissions efficiently. For example, if a company expands its sales team from 50 to 500 employees, the CRM system should be able to accommodate this growth without performance degradation or administrative bottlenecks.
A flexible RBAC system allows for customization to align with unique business processes and requirements. This includes the ability to create custom roles, define granular permissions, and integrate with other security systems. For example, a healthcare organization might need to create roles specifically for “Patient Care Coordinators” with access to patient records but restricted access to financial data. The CRM should support this level of customization.
The CRM should integrate with other security systems, such as identity and access management (IAM) platforms and single sign-on (SSO) solutions. This integration streamlines user authentication and authorization, enhances security, and simplifies user management. For example, integrating the CRM with an IAM platform allows users to log in using their existing credentials and ensures consistent access controls across all systems.
The CRM should incorporate security features such as multi-factor authentication (MFA), encryption, and data masking. MFA adds an extra layer of security by requiring users to provide multiple forms of verification. Encryption protects data at rest and in transit. Data masking hides sensitive information from unauthorized users. These features help to protect data from unauthorized access and breaches.
Importance of RBAC in Relation to CRM System Scalability
RBAC plays a vital role in the scalability of a CRM system. As an organization grows, the number of users, the volume of data, and the complexity of business processes increase. A well-designed RBAC system can help manage this complexity and ensure that the CRM system remains secure, efficient, and compliant.
- Simplified User Management: RBAC simplifies user management.
- Improved Data Security: RBAC enhances data security.
- Enhanced Compliance: RBAC supports regulatory compliance.
- Efficient System Performance: RBAC can contribute to improved system performance.
Instead of managing individual user permissions, administrators can assign users to roles, which define their access rights. This approach reduces the administrative overhead and minimizes the risk of human error. For example, when a new sales representative joins the company, the administrator only needs to assign them the “Sales Representative” role, and the appropriate permissions are automatically applied.
By restricting access to sensitive data, RBAC reduces the risk of unauthorized access and data breaches. Granular permissions and role hierarchies allow administrators to control who can view, edit, or delete specific data fields. This protects sensitive customer information and ensures compliance with data privacy regulations.
For instance, in a financial services CRM, access to customer financial data can be strictly limited to authorized financial advisors and compliance officers.
Many data privacy regulations, such as GDPR and CCPA, require organizations to implement access controls to protect sensitive data. RBAC helps organizations comply with these regulations by providing the tools to manage user access and track user activity. Audit trails generated by RBAC systems are essential for demonstrating compliance. For example, a healthcare organization using a CRM to manage patient data must comply with HIPAA regulations, which require strict access controls and audit trails.
By optimizing user access, RBAC can reduce the load on the CRM system. When users only have access to the data and functionality they need, it reduces the amount of data that the system must process. This can improve system performance and responsiveness. For example, by limiting the number of users who can access and modify large datasets, the system can maintain optimal performance.
Advanced RBAC Techniques: Dynamic Role Assignment
Dynamic role assignment represents a significant advancement in Role-Based Access Control (RBAC) within CRM systems. Instead of static role assignments, this approach allows for real-time adaptation of user privileges based on various factors, enhancing both security and operational efficiency. This flexibility is crucial in modern CRM environments where user needs and data access requirements are constantly evolving.
Dynamic Role Assignment Techniques Based on Attributes or User Behavior
Dynamic role assignment leverages real-time data and triggers to adjust user permissions. This can be based on a variety of criteria, enabling a more granular and responsive approach to access control.
- Attribute-Based Assignment: This technique assigns roles based on user attributes or data characteristics. This includes user profile information (e.g., department, job title, location), data attributes (e.g., customer segment, deal stage), or a combination of both.
- Behavior-Based Assignment: This approach dynamically adjusts roles based on user actions and CRM system usage patterns. For example, if a user consistently accesses data related to a specific product line, their role might be automatically updated to grant them broader access to information relevant to that line.
- Time-Based Assignment: Roles can be assigned or modified based on the time of day, day of the week, or specific events. This is particularly useful for managing access during specific campaigns, after-hours support, or during periods of increased activity.
- Context-Aware Assignment: This method considers the context of the user’s access request. This includes the user’s device, location, network, and the specific data they are attempting to access.
Examples of How Dynamic Role Assignment Can Improve Security and Efficiency in a CRM, Role-Based Access in CRM: Least Privilege by Design
Dynamic role assignment enhances both security and efficiency by adapting access control to real-time conditions. These examples highlight its practical benefits.
- Improved Security: Consider a scenario where a CRM user, a sales representative, is traveling to a customer site. The system could automatically grant the representative temporary elevated access to sensitive customer data based on their location (e.g., within a defined geographical area), only for the duration of their visit. Once the representative leaves the area, their access rights revert to their standard profile.
This minimizes the risk of unauthorized access and data breaches.
- Enhanced Efficiency: Imagine a marketing campaign that requires specific CRM data access for a limited time. Instead of manually assigning and revoking roles for each user involved, the system can automatically grant access to the relevant data based on a predefined schedule or trigger (e.g., campaign start and end dates). This automates the process, saving time and reducing the potential for human error.
- Adaptive Access Control: A user’s role can change dynamically based on their performance metrics or customer interaction history. For example, if a sales representative consistently closes a high volume of deals, the system might automatically promote them to a role with greater data access and decision-making authority.
- Compliance with Regulations: Dynamic role assignment can facilitate compliance with data privacy regulations such as GDPR or CCPA. By dynamically restricting access to sensitive data based on a user’s role and context, organizations can minimize the risk of non-compliance and data breaches.
Visual Representation of Dynamic Role Assignment in a CRM Environment (Flowchart)
The following flowchart illustrates the process of dynamic role assignment in a CRM.
Flowchart Description:
The flowchart begins with a “User Action/Request” box. This initiates the process. The flow then proceeds to a “Trigger Identification” box. This box determines the triggering event, such as a user attribute change, a time-based event, or a specific user behavior.
Next is a decision diamond, “Trigger Met?”. If “Yes”, the process goes to “Role Assignment/Modification” box, where the user’s role is dynamically adjusted based on the identified trigger. If “No”, the process goes to “Standard Role Applied”. Both branches then converge to the “Access Granted/Denied” box, where access is determined based on the updated (or standard) role. Finally, the process ends.
The chart also includes a feedback loop, where the “User Action/Request” feeds back into the “Trigger Identification” box, allowing for continuous monitoring and adjustment.
[Flowchart Image (Descriptive)]
The flowchart provides a clear visual representation of the dynamic role assignment process, highlighting the key steps involved in adapting user permissions based on real-time triggers and conditions within a CRM system.
RBAC in the context of CRM Integrations
Role-Based Access Control (RBAC) is crucial for maintaining data security and operational efficiency within a CRM, and its importance extends significantly when the CRM is integrated with other systems. These integrations, whether they involve marketing automation platforms, customer support systems, or financial tools, introduce new access points and potential vulnerabilities. Effective RBAC implementation ensures that user access and data visibility are consistently managed across the entire ecosystem, minimizing the risk of unauthorized data access and promoting compliance with data privacy regulations.Understanding and properly managing user access and permissions across integrated systems is paramount for maintaining data integrity and security.
Without proper control, users could inadvertently or maliciously access data they are not authorized to view or modify, leading to breaches, compliance violations, and operational inefficiencies. Careful consideration must be given to how roles and permissions defined within the CRM are mapped and translated to the integrated systems. This process involves defining clear access policies, establishing robust authentication and authorization mechanisms, and regularly auditing user access across all platforms.
Managing User Access and Permissions Across Integrated Systems
Successfully managing user access and permissions across integrated systems requires a multi-faceted approach. This includes a thorough understanding of the data flow between systems, the specific permissions required for each integration, and the security protocols of each platform involved. Centralized user management, where user identities and permissions are managed from a single source (often the CRM), is a best practice, simplifying administration and reducing the likelihood of inconsistencies.
- Identity Synchronization: Establish a mechanism for synchronizing user identities and roles between the CRM and integrated systems. This can involve using Single Sign-On (SSO) solutions, directory services (e.g., Active Directory), or dedicated identity management platforms.
- Permission Mapping: Define clear mappings between CRM roles and the corresponding permissions in integrated systems. This may involve creating equivalent roles in the integrated systems or mapping CRM roles to specific permission sets.
- Data Governance: Implement data governance policies to control how data is accessed, used, and shared across integrated systems. This includes defining data ownership, establishing data quality standards, and implementing data masking or anonymization techniques where necessary.
- Regular Auditing: Conduct regular audits of user access and permissions across all integrated systems. This helps identify and address any unauthorized access or permission discrepancies. Audit logs should be reviewed regularly to detect any suspicious activity.
- Least Privilege Principle: Apply the least privilege principle consistently across all systems. Users should only be granted the minimum necessary access required to perform their job functions.
RBAC Considerations for Common CRM Integrations
The following table illustrates RBAC considerations for common CRM integrations. Each integration type presents unique challenges and requires tailored access control strategies. These considerations are based on best practices and industry standards for data security and compliance.
| Integration Type | RBAC Considerations | Example Access Control Scenario | Potential Risks if RBAC is Inadequate |
|---|---|---|---|
| Marketing Automation |
| A “Campaign Manager” role has access to create and manage marketing campaigns, view customer segments, and analyze campaign performance, but cannot modify customer contact details or access sensitive data. | Unauthorized access to customer data, data breaches through email campaigns, and non-compliance with data privacy regulations (e.g., GDPR, CCPA). |
| Customer Support Platforms |
| A “Tier 1 Support” role has access to view and respond to customer support tickets, but cannot access customer payment information or modify support ticket assignments. | Data breaches of customer support communications, unauthorized access to customer payment information, and failure to comply with data privacy regulations. |
| Financial Systems |
| A “Sales Representative” role has access to view sales orders and customer payment history but cannot modify financial reports or access detailed transaction data. | Unauthorized access to financial data, data breaches of payment information, and fraudulent financial transactions. |
| Sales Automation |
| A “Sales Manager” role has access to view sales forecasts, monitor team performance, and access lead data, but does not have the ability to change commission structures or access highly sensitive pricing information. | Unauthorized access to sales data, data breaches of pricing information, and manipulation of sales forecasts. |