Aloo, kawan-kawan! CRM Security in 2025: SSO, SCIM, BYOK, and Data Residency Explained. In the year 2025, the security of your customer relationship management (CRM) system is more important than ever, sanak. We’re talkin’ about protecting precious data from all sorts of threats, from the usual suspects to the new, unexpected ones. Data privacy and following the rules are getting stricter, so we gotta be ready.
This exploration is a journey to learn about how we can keep our CRM systems safe and sound, like a good, sturdy rumah gadang. We’ll be lookin’ at some important tools and strategies, like Single Sign-On (SSO) to make things easy, SCIM for managing user access automatically, Bring Your Own Key (BYOK) to keep your data secret, and data residency to make sure your data lives where it should.
So, come along, and let’s figure out how to keep our CRM systems secure in 2025!
Introduction: The Evolving Landscape of CRM Security in 2025: CRM Security In 2025: SSO, SCIM, BYOK, And Data Residency Explained
In the dynamic landscape of 2025, Customer Relationship Management (CRM) systems have become indispensable for businesses of all sizes. However, this increased reliance on CRM for managing sensitive customer data has also made them prime targets for cyberattacks. Consequently, CRM security has evolved from a mere IT concern to a critical business imperative. The threats are becoming more sophisticated, and data privacy regulations are becoming stricter, necessitating a proactive and comprehensive approach to CRM security.
The significance of robust CRM security in 2025 stems from the critical role these systems play in managing customer interactions, storing confidential data, and driving business operations. Breaches can lead to significant financial losses, reputational damage, and legal consequences. The increasing sophistication of cyber threats, including ransomware, phishing attacks, and insider threats, further elevates the risks. Moreover, the rising expectations of data privacy, driven by regulations like GDPR, CCPA, and others, mandate stringent compliance measures within the CRM environment.
SSO (Single Sign-On) in CRM Security, CRM Security in 2025: SSO, SCIM, BYOK, and Data Residency Explained
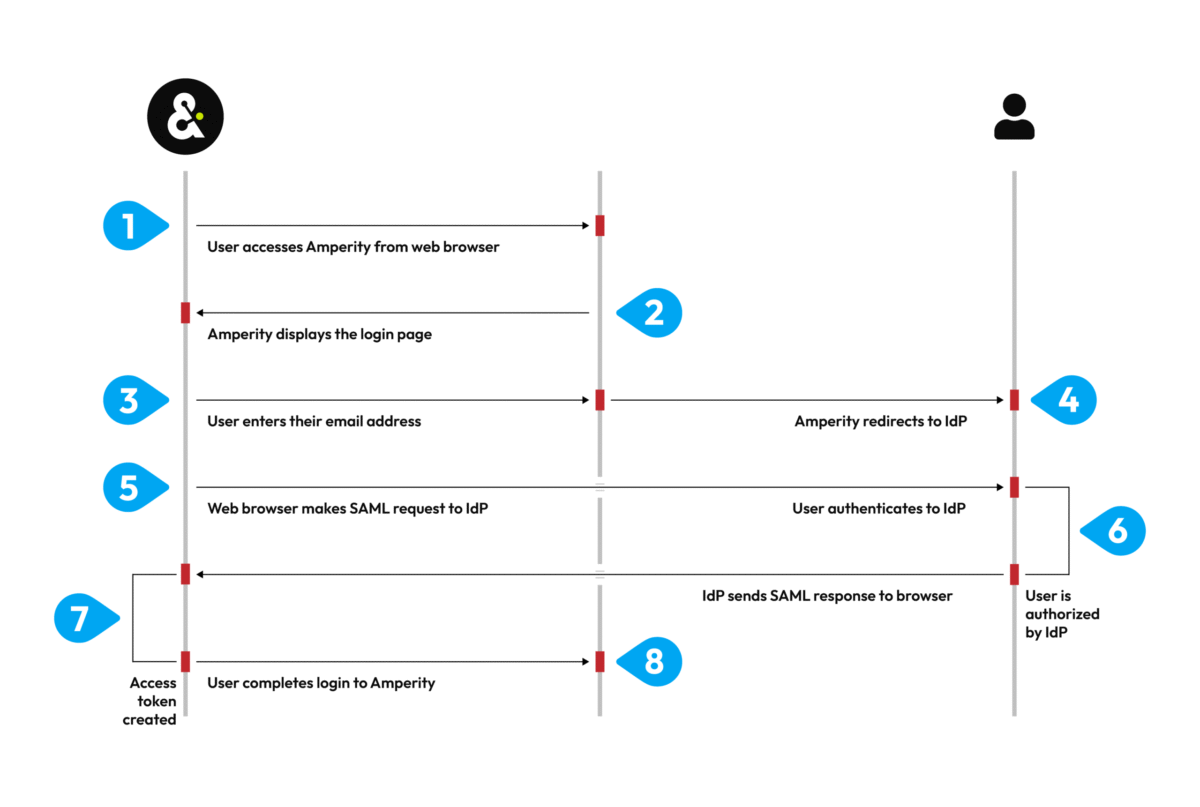
Source: amperity.com
Single Sign-On (SSO) offers a streamlined and secure approach to accessing CRM systems, enhancing both user experience and security posture. By allowing users to authenticate once and access multiple applications, SSO eliminates the need for multiple passwords, reducing the risk of password fatigue and related vulnerabilities. This approach also simplifies access control and centralizes user management, making it easier to enforce security policies.
Understanding CRM security in 2025, including SSO, SCIM, BYOK, and data residency, is crucial. However, the best security measures are useless if you choose the wrong CRM. For a 5-20 person sales team, the choice between HubSpot and Pipedrive is critical, and you can find a detailed comparison here: HubSpot vs Pipedrive in 2025: Which CRM Is Best for a 5–20 Person Sales Team?
Ultimately, a robust security posture starts with selecting a CRM that aligns with your needs and security protocols.
Several SSO protocols are commonly used with CRM systems, each with its strengths and weaknesses. These protocols facilitate secure authentication and authorization, ensuring that only authorized users can access sensitive data. Choosing the right protocol depends on the specific CRM system and the organization’s security requirements.
While understanding CRM Security in 2025, with its SSO, SCIM, BYOK, and data residency considerations, is crucial, real estate professionals also need to focus on efficiency. Implementing automation to book more viewings, as detailed in the article on CRM for Real Estate 2025: Automation That Books More Viewings , can significantly boost productivity. However, remember that enhanced security measures are essential to protect sensitive client data in this increasingly automated landscape.
- SAML (Security Assertion Markup Language): A widely adopted standard for exchanging authentication and authorization data between identity providers (IdPs) and service providers (SPs). SAML provides robust security features and supports various authentication methods.
- OAuth 2.0: An open standard for authorization that allows users to grant third-party applications access to their resources without sharing their credentials. OAuth 2.0 is commonly used for web and mobile applications.
- OpenID Connect (OIDC): An identity layer built on top of OAuth 2.0, providing authentication and user profile information. OIDC simplifies the integration of SSO with various applications.
Integrating SSO into a CRM system typically involves the following steps:
- Choose an SSO Provider: Select an SSO provider that supports the desired SSO protocol and integrates with the CRM system.
- Configure the SSO Provider: Set up the SSO provider with the necessary information, such as the CRM system’s URL and authentication endpoints.
- Configure the CRM System: Configure the CRM system to trust the SSO provider and accept authentication assertions from it.
- Test the Integration: Test the SSO integration to ensure that users can successfully authenticate and access the CRM system.
- Deploy and Monitor: Deploy the SSO integration and monitor it for any issues.
Here’s a comparison of the pros and cons of different SSO methods:
| SSO Method | Pros | Cons | Use Cases |
|---|---|---|---|
| SAML | Widely supported, robust security, supports various authentication methods | Can be complex to configure, requires a dedicated identity provider | Enterprise applications, highly secure environments |
| OAuth 2.0 | Easy to implement, supports mobile and web applications, flexible authorization | Less secure than SAML, requires careful configuration, potential for authorization vulnerabilities | Web applications, mobile apps, third-party integrations |
| OpenID Connect | Simple to implement, provides user profile information, built on OAuth 2.0 | Requires an identity provider, less secure than SAML | Web applications, mobile apps, social login |